Be Aware of SIM Swap Attacks
IT Security, Social EngineeringPhone number theft is more possible – and prevalent – than you might think. Hackers are deploying attacks known as SIM swap attacks and the damage might be more than you would expect. This article discusses everything you need to know about SIM swap fraud and how to better protect yourself.
The SIM card inside your phone is a small plastic chip that tells your device which cellular network to connect to, and which phone number to use. We hardly think twice about SIM cards and that is part of the problem. Hackers know that SIM cards are a fairly easy access point when it comes to taking over someone’s phone number, and then gaining access to online accounts. Most people though don’t understand the significance of this attack and what can be done once a phone number has been taken over.
Twitter CEO Falls Victim to SIM Swap Attack
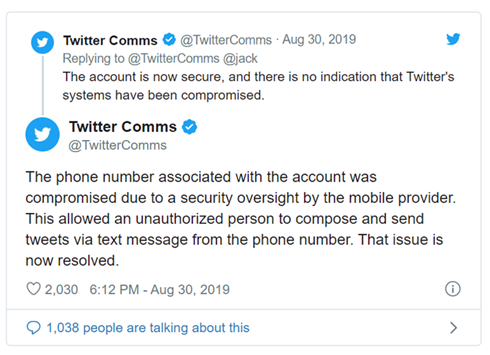
If you are thinking that this type of attack really doesn’t happen, know that even Twitter’s CEO and co-founder Jack Dorsey fell victim to a SIM swap attack back in August of 2019 with the people responsible tweeting sexist, racist and anti-Semitic comments, as well as bomb threats. “The phone number associated with the account was compromised due to a security oversight by the mobile provider,” Twitter Comms tweeted. “This allowed an unauthorized person to compose and send tweets via text message from the phone number. That issue is now resolved.”
So how does this attack happen?
For this attack, a hacker will utilize social engineering techniques to convince your wireless carrier to switch the SIM card linked to your phone number and replace it with a SIM card in the hacker’s possession. Once this occurs, all your incoming calls and text messages will be routed to whatever phone the new SIM card is in.
So, what’s the big deal…?
At first glance, this may seem somewhat harmless, but when you stop to think about the accounts you have linked to your phone (bank, email, social media, etc.) you begin to realize the significance of a SIM swap attack. A successful SIM swap attack can take over your entire online presence.
Take this scenario for example: A hacker took over an individual’s phone number and gained access to the individual’s Gmail account and proceeded to delete every file in Google Drive and eventually deleted the Gmail account altogether. The hacker also gained access to the individual’s bank account because the individual’s phone received the account’s two-factor authentication codes.
That’s the big one for hackers. A SIM swap attack will allow the hacker instant access to any two-factor authentication codes that you receive through text messages. That means if the hacker has your password, they’re just a few clicks away from logging into all your accounts, even if you have set up SMS based two-factor authentication. Take the time to move away from SMS based two-factor authentication.
How do you know if you’ve been compromised?
A telltale sign that you’ve been compromised is if you completely lose service on your phone. If your SIM card is no longer active, you won’t be able to place a call from your phone. You may receive a text message stating that the SIM card for you number has been changed – that’s obviously a red flag. Once you realize that you’ve lost service on your mobile device, its crucial that you call your carrier immediately and let them know that you did not make the changes. You’ll also want to reach out to your bank(s), credit card company(s), and double-check all of your online accounts.
What steps can you take to prevent SIM swapping from happening to you?
You can decrease the chances of someone taking over your phone number by adding a PIN code or password to your wireless accounts. Verizon, AT&T, T-Mobile and Sprint all offer this. Some companies require this when you sign up for the service. If you are unsure if you have a PIN code or if you need to set one up, here are steps to take for each of the four major US carriers.
- Sprint customers: Log in to your account on Sprint.com then go to My Sprint > Profile and security > Security information and update the PIN or security questions then click Save.
- AT&T subscribers: Go to your account profile, sign in, and then click Sign-in info. Select your wireless account if you have multiple AT&T accounts, then go to Manage extra security under the Wireless passcode section. Make your changes, then enter your password when prompted to save.
- T-Mobile users: Set up a PIN or passcode the first time you sign in to your My T-Mobile account. Pick Text messages or Security question and follow the prompts.
- Verizon Wireless customers: Call *611 and ask for a Port Freeze on your account, and visit this webpage to learn more about enabling Enhanced Authentication on your account.
But here is the deal, if someone wants access to your phone number bad enough, they will do all they can to social engineer your carrier’s support representative. If you have a PIN code or password linked to your account, that’s good because it’s an extra layer of security, but when it comes down to it, that is a layer of security that can be easily compromised by a skilled social engineer.
A hacker could call in posing as an account holder who has forgotten the PIN or password and researchers have proven this out. They tell the support representative that they don’t remember their passcode and then provided the recent numbers called by the account holder. How do they know those numbers? They either tricked the account holder into calling a couple of numbers – or even scarier, phone numbers for incoming calls to the account they want to take over, meaning the hacker simply needed to call the target’s phone number themselves.
Princeton University Study on SIM Swapping
A Princeton University academic study published at the beginning of this year found that five major US prepaid wireless carriers are vulnerable to SIM swapping attacks. In 2019, Princeton academics spent their time testing five major US telco providers to see if they could trick call center employees into changing a user’s phone number to another SIM without providing proper credentials.
According to the research team, AT&T, T-Mobile, Tracfone, US Mobile, and Verizon Wireless were found to be using vulnerable procedures with their customer support centers, procedures that attackers could use to conduct SIM swapping attacks.
In addition, the research team also looked at 140 online services and websites and analyzed on which of these attackers could employ a SIM swap to hijack a user’s account. According to the research team, 17 of the 140 websites were found to be vulnerable.
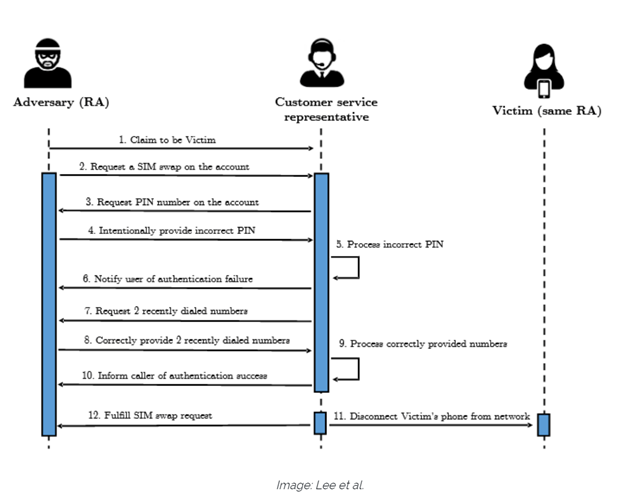
In the picture above, the adversary would call a telco’s support center to request a SIM card change and then intentionally provide an incorrect PIN and account owner details such as date of birth, billing ZIP code, etc. The telco representative would let the adversary know that the information was incorrect. At this point, after failing the first two authentication mechanisms (PIN and account owner details), telco operators are required, based on their procedures, to move to a third mechanism. The third mechanism used by the telco companies was to ask the account owner (at this point the adversary) to provide details about the last two recent calls. These can be obtained by tricking the victim into placing calls to specific numbers. Once the adversary has provided the telco representative with the last two calls made by the victim, the telco representative will fulfill the SIM swap request, ultimately disconnecting the victims phone and providing the adversary with the ability to obtain SMS based tokens.
Here are three signals you may be a victim of SIM swapping:
- You’re unable to place calls or texts. The first big sign that you could be a victim of SIM swapping is when your phone calls and text messages aren’t going through. This likely means fraudsters have deactivated your SIM and are using your phone number.
- You’re notified of activity elsewhere. You’ll know you’re a victim if your phone provider notifies you that your SIM card or phone number has been activated on another device.
- You’re unable to access accounts. If your login credentials no longer work for accounts like your bank and credit card accounts, you likely have been taken over. Contact your bank and other organizations immediately.
How can you protect yourself from SIM swap scams?
Here are ways you can help protect yourself against becoming a victim of SIM swap fraud.
- Online behavior: Beware of phishing emails and other ways attackers may try to access your personal data to help them convince your bank or cell phone carrier that they are you.
- Account security: Boost your cellphone’s account security with a unique, strong password and strong questions-and-answers (Q&A) that only you know.
- PIN codes: If your phone carrier allows you to set a separate passcode or PIN for your communications, consider doing it. It could provide an additional layer of protection.
- IDs: Don’t build your security and identity authentication solely around your phone number. This includes text messaging (SMS), which is not encrypted.
- Authentication apps: You can use an authentication app such as Google Authenticator, which gives you two-factor authentication but ties to your physical device rather than your phone number.
- Bank and mobile carrier alerts: See if your banks and mobile carrier can combine efforts, sharing their knowledge of SIM swap activity, and implementing user alerts along with additional checks when SIM cards are reissued, for instance.
- Behavioral analysis technology: Banks can use technology that analyzes customer behavior to help them discover compromised devices.
- Call-backs: Some organizations call customers back to make sure they are who they say they are — and to catch identity thieves.
Article Written By: Chad Gutschenritter
For more information, check out the following:
https://www.issms2fasecure.com/assets/sim_swaps-01-10-2020.pdf
https://www.issms2fasecure.com/dataset
https://us.norton.com/internetsecurity-mobile-sim-swap-fraud.html
https://lifehacker.com/how-to-prevent-and-respond-to-a-sim-swap-scam-1835627474